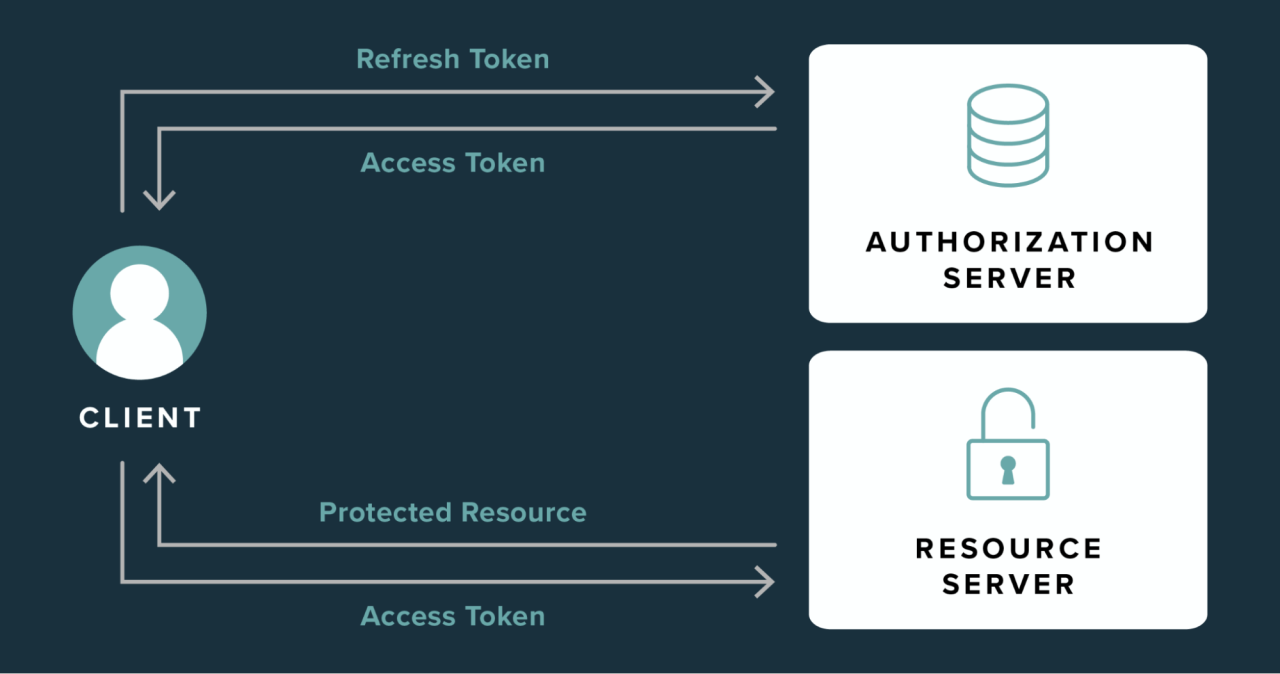
Securing a backend is like managing a grand concert hall. Every guest must show a ticket at the door, but once inside, you don’t want to check their identity at every row of seats. JSON Web Tokens (JWTs) operate similarly—handing each “guest” a digital ticket that grants them access without constant revalidation. This stateless approach enables backend security to be both efficient and scalable, particularly in modern distributed applications.
The Stateless Promise of JWT
JWTs differ from traditional session-based authentication by removing the need for the server to hold on to user session data. Instead, the token itself carries all the necessary information, signed and tamper-proof.
Picture it like a stamped boarding pass on a flight: the airline doesn’t keep track of each passenger’s paper ticket, but the stamp itself assures validity. This shift reduces server load and simplifies scaling applications across multiple nodes, which is critical for cloud-native systems.
Anatomy of a Token
A JWT looks unassuming—a compact string separated by dots—but within lies the structure of a well-organised lockbox. It’s composed of three parts:
- Header: Identifies the signing algorithm.
- Payload: Contains user claims and data.
- Signature: Verifies integrity and authenticity.
This triad ensures that even if a token is intercepted, it cannot be altered without breaking the signature. Developers studying security concepts in full-stack classes often find JWTs a perfect entry point into real-world authentication challenges.
Implementation in Modern Backends
When a user logs in, the server generates a JWT with their information and signs it with a secret key. From then on, each request includes the token, which the server validates without storing session data.
This model works beautifully in distributed systems where multiple servers or microservices share the responsibility of responding to requests. Because JWTs are self-contained, any service with the signing key can validate them, avoiding the bottleneck of centralised session storage.
Balancing Security and Usability
JWTs offer speed and simplicity, but like any tool, they come with responsibilities. Token expiration, secure storage, and refresh mechanisms must be handled carefully. A token that lives too long is like a master key that can open doors long after it should.
Developers pursuing a full-stack classes curriculum often experiment with building secure login flows, learning firsthand how to configure expiry times, refresh strategies, and role-based access. This practical exposure highlights the balance between airtight security and seamless user experience.
Conclusion
JWT authentication brings a stateless, elegant solution to backend security, much like issuing secure tickets at the entrance of a concert. It allows applications to scale gracefully while maintaining control over access and identity.
By understanding the structure, implementation, and pitfalls of JWTs, developers can design systems that withstand the pressures of modern traffic and distributed environments with confidence. With practice and the right learning approach, JWTs move from an abstract concept to a trusted ally in crafting robust backend architectures.